Under the name "Dark Skippy", Lloyd Fournier, Nick Farrow and Robin Linus yesterday demonstrated an attack that can be used to publish the private keys of a Bitcoin hardware wallet via manipulated signature data. With just two or four such manipulated signatures, it should be possible to extract the 12 or 24 words of the wallet and gain full control over the Bitcoin stored there. The prerequisite for the attack is a malicious hardware wallet or a malicious signing device that specifically attempts to attack its own user.
Let's take a look at the new attack - which is actually anything but new - and how you can protect yourself against it!
Today we introduce Dark Skippy - a powerful new method by which a malicious signing device can publish private keys.
Using a spoofed signature method, a device can efficiently and covertly exfiltrate a secret master seed by embedding it in transaction signatures.
@utxoclub on 𝕏
Trojan signatures
The Dark Skippy approach, i.e. the manipulation of Bitcoin signatures to hide secret information in them, is basically anything but new and has been known in the world of hardware wallets for some time. There is therefore no reason to panic at first, as no ground-breaking discovery has been made, but merely built on an existing concept, including a demonstration in practice.
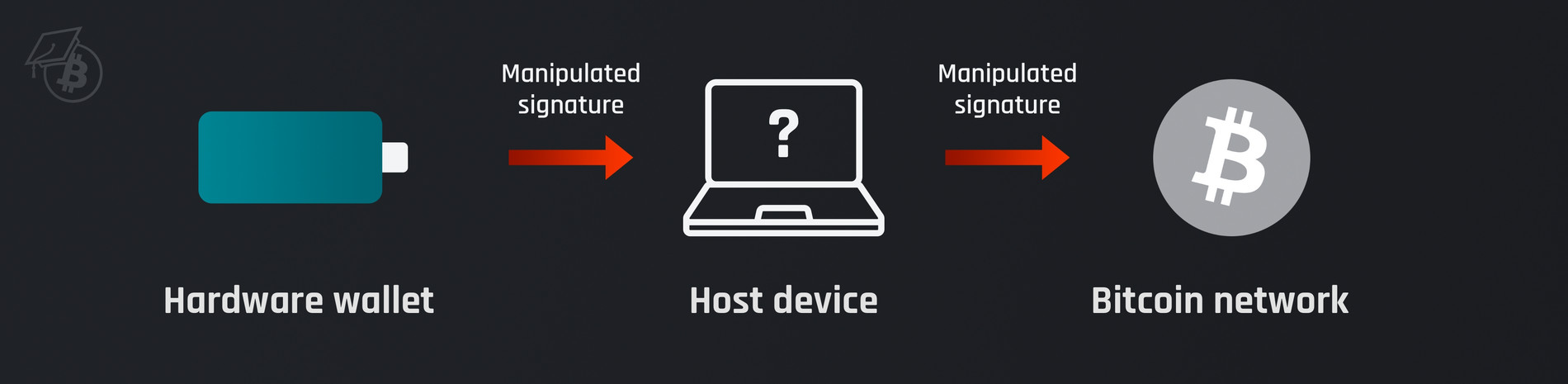
But what is it all about? The basic assumption of attacks with "manipulated signatures" is a compromised, i.e. malicious, hardware wallet. At first, you might assume the worst in such a scenario, because if you can't trust your own hardware wallet, who can you trust?
In practice, however, it is not so easy for malicious hardware wallets to publish the user's seed, e.g. the wallet's 24 recovery words, to the outside world - after all, the hardware wallet has no direct connection to the Bitcoin network or the Internet.
A hidden communication channel
For the specific scenario in which a malicious hardware wallet wants to publish the user's seed to an attacker after the fact, the so-called "nonce covert channel attack" comes into play, which in simple terms means misusing a certain area of a digital signature as a data field in order to publish information on the Bitcoin network without the end device noticing.
In such an attack, the attacker only has to look for the right transaction in the network and can simply read out the secret, e.g. a single word. The special feature of this method is that the manufacturer of a hardware wallet could, at least theoretically, read the seed words of its customers in this way without anyone noticing.
Even with reproducible open-source firmware, this theoretical risk cannot be ruled out, as it is basically impossible to really verify which code is ultimately executed inside a hardware wallet.
Really relevant?
It is not without reason that this attack has often been dismissed as too theoretical or specific in the past, as the comparatively high technical complexity could quickly deter a potential attacker. In order to successfully export a whole 24 words, several dozen manipulated signatures would be necessary, which would require a lot of computing capacity to create.
On the other hand, a compromised hardware wallet has other ways of accessing the user's Bitcoin. Probably the simplest example would be predetermined seed words, where the user thinks they are creating a random wallet, but in reality only retrieves a prepared wallet from the attacker. Another, but equally effective option would be to communicate false public keys to the end device in order to simulate false addresses for the user.
However, these two "more primitive" attack methods are not ideal. After all, the user could roll their own seed and/or verify the derivation of the addresses with an independent device. Furthermore, these methods could not be used retrospectively, e.g. with a manipulated firmware update.
The covert route via the manipulated signatures is therefore not so irrelevant after all, as firstly it can be carried out undetected and above all retrospectively, regardless of whether the user uses their own seed or not. If only it were more efficient...
Dark Skippy
The new Dark Skippy attack method uses the approach just explained, but above all improves its efficiency. Previously, it was always assumed that the hardware wallet would have to "test" many different random numbers (also known as "nonces") when creating the signature until it received the desired manipulated signature. The longer the desired message, the more complex and ultimately unrealistic the attack - hence the many signatures required for success.
Dark Skippy changes the approach in that it is no longer necessary to test so many different random values at great expense. Instead, by using a smaller, specifically selected random number and then applying an algorithm to the signatures, a much larger amount of random data can be transmitted in a single signature. For example, 12 words would require just two signatures and 24 words just four. In other words, a single transaction could theoretically publish a user's entire wallet secret.
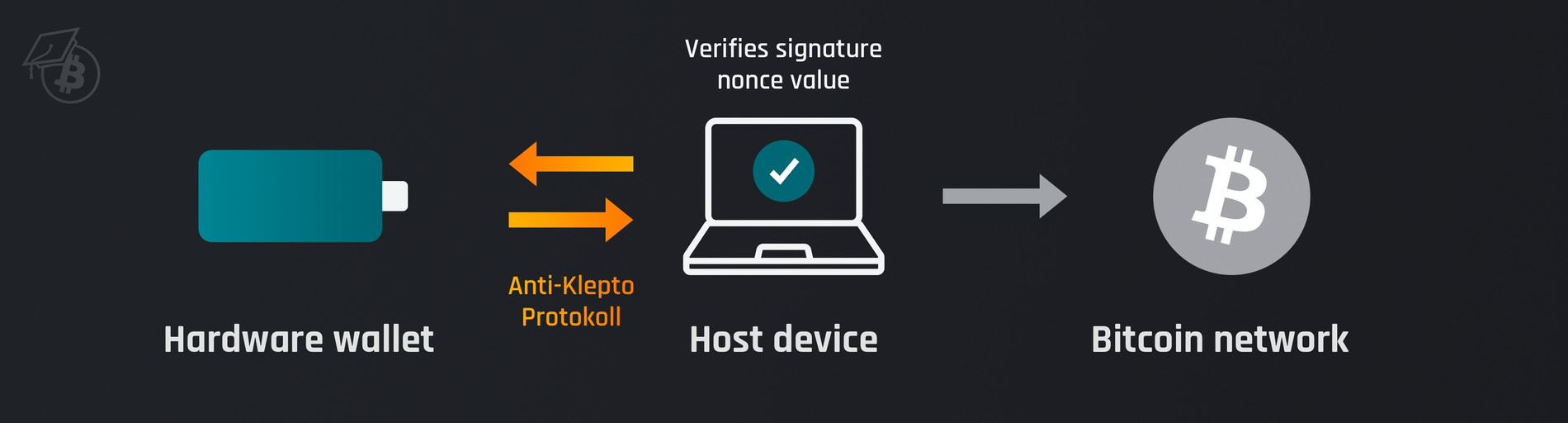
Anti-Klepto Protocol
Fortunately, there is already an established countermeasure that prevents both dark skippy and the manipulation of signatures themselves. With the Anti-Klepto protocol, the end device is directly involved in the creation of the signature, or more precisely in the selection of the random number or nonce. The protocol is designed in such a way that the hardware wallet has no way of determining the nonce of the signature on its own without the end device noticing. The wallet software on the end device can therefore cryptographically verify that no signatures have been manipulated and thus render the attack scenario null and void.
There are currently two hardware wallets that have implemented the Anti-Klepto or Anti-Exfil protocol: the Blockstream Jade and the BitBox02. Anti-Klepto is not only compatible with the in-house wallet software, i.e. Blockstream Green or the BitBoxApp, but is also part of the HWI (Hardware Wallet Interface) and is therefore also activated when using software such as Electrum or Sparrow Wallet. As part of the official cryptography library of Bitcoin Core, the protocol is also available for other manufacturers to integrate into their own products. Support for Taproot addresses is already being worked on.
For air-gapped wallets, which are deliberately limited in the bandwidth of communication with the end device, the implementation of the Anti-Klepto protocol is not quite so simple. Firstly, because no one has yet taken the trouble to design or implement a corresponding procedure and secondly, because it would complicate the user experience in some way. Additional rounds of communication and the exchange of a higher volume of data would be necessary.
Conclusion
So has Dark Skippy made all other hardware wallets and signing devices insecure? No, that would be quite an exaggeration. In the course of the article, it should have become clear that this is a rather advanced attack method that can only be implemented with a great deal of effort, technical expertise and a high degree of control over a specific hardware wallet. So far, no successful attacks have been reported in practice, although Dark Skippy has of course only just been introduced or demonstrated as a more efficient attack.
The Anti-Klepto protocol is primarily a security feature that requires users to place less trust in the manufacturer of the hardware wallet. The risk of such an attack is therefore verifiably excluded. There will probably never be a completely "trustless" hardware wallet, but it is still worth constantly optimizing security and trust assumptions and making the self-custody of Bitcoin a little more secure.