In addition to the optional passphrase, multi-signature wallets are among the most popular measures to increase the security of your Bitcoin. However, none of these functions come without some treacherous pitfalls. In this article, we take a look at why almost all regular multisig setups are used in a relatively insecure manner and why, despite expensive hardware wallets, nothing can be achieved if certain basic rules are disregarded. Have fun with this multisig deep dive!
Why Multisig?
If the security of a simple wallet, which only requires one signature for a valid transaction, is not enough, multisig can be used to introduce any number of additional factors, i.e. the need for multiple signatures. With a classic 2-out-of-3 split, in which two out of a total of three private keys must sign a transaction, additional protection against theft is introduced. It also creates redundancy, as one of the keys can easily be lost - after all, you only need two out of three when it comes down to it.
In addition, there are of course other, purely practical, use cases for multisig wallets, e.g. for managing Lightning channels. At this point, however, we are only interested in the security use case from the perspective of a simple user.
The first thing they need to think about is how and to which devices the various keys should be distributed. We will refer to these "co-signers" as cosigners in the following. This is where the first stumbling block becomes apparent...
1. Dangerous cocktail
If you already use a hardware wallet and want to "upgrade" to multisig, you are usually faced with quite high acquisition costs. For a sensible and practicable 2-out-of-3 split, you need three hardware wallets - which is not exactly cheap.
It is therefore tempting to make compromises in terms of security, e.g. by using a simple software wallet together with two hardware wallets. However, this apparently sensible compromise turns out to be a mistake that can undermine the security of the entire wallet.
Hardware wallets are used because all the software on the smartphone or computer cannot be trusted. These are always potentially compromised by attackers. This is exactly what you would have to assume with the software wallet in a 2-out-of-3 setup. But that's not a problem, is it? After all, a signature on the software wallet is not sufficient for a valid transaction?
Address, where are you from?
To understand the background to this, you need to understand exactly how the receive addresses of a multisig wallet are created in the first place. After all, these must contain all the information about the setup so that it is clear to the Bitcoin network when the conditions are met to issue Bitcoin.
An address of a 2-of-3 setup therefore contains the public keys of all three cosigners. In order to generate a correct address, you must therefore be able to rely on all cosigners equally.
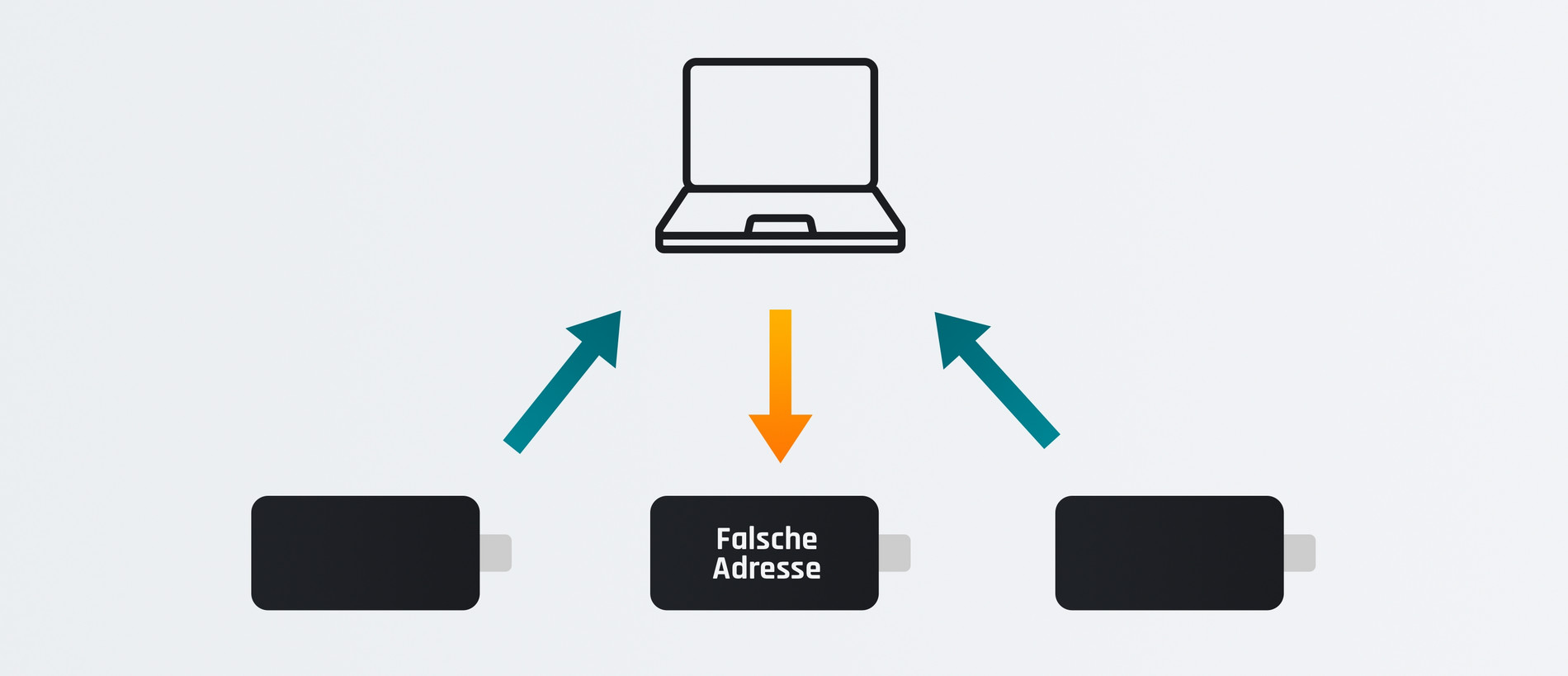
Despite the use of two hardware wallets, the software wallet from the example above could contribute a forged public key to generate the receiving addresses. After all, the hardware wallets simply have to accept the information from the other cosigners and have no way of verifying it. The resulting address would no longer have anything to do with your own multisig wallet and would belong to another wallet to which you have no access.
This would put the operator, or the person who compromised the software wallet, in a position where they could blackmail the user with a ransom in order to release the third key foisted on them by the fake software. A very unpleasant idea that no longer has much to do with "security gained".
Such scenarios are of course quite contrived and seem unrealistic at first glance. But this is exactly the kind of sophisticated attack you want to protect yourself against with a multisig wallet! Otherwise, you might as well leave it at a simple hardware wallet, which already provides sufficient protection against the vast majority of threats.
Note: The security of a multisig wallet is always measured by the "least secure" cosigner, i.e. the biggest vulnerability. Therefore, all cosigners should always have a comparably high level of security. Mixing hot and cold wallets is therefore contradictory and not recommended.
2. Incomplete backups
At first glance, the topic of backups seems trivial: with a 2-of-3 multisig wallet, three backups must be stored, preferably separately and securely. Only two of these backups are then necessary in an emergency to restore the wallet and its Bitcoin.
Unfortunately, this is not entirely correct. Although two of the backups would be enough to spend Bitcoin from the wallet, it must first be clear what you want to spend in the first place. The addresses of the wallet must first be reassembled - for which you need all three public keys of all cosigners.
Note: All extended public keys (xpubs) or those of the remaining cosigners should be noted on every backup of a multisig wallet so that the wallet addresses can always be restored in an emergency.
3. Problematic verification
The security of a multisig wallet stands and falls with the generation and, above all, verification of receiving addresses. This Achilles' heel was already more or less part of the first two stumbling blocks, but is only now becoming really crucial.
Hardware wallets without their own display are pretty useless, because information displayed by the wallet software on the smartphone or computer cannot otherwise be verified for correctness. But with a multisig setup, this fact is taken even further: even information on the displays of hardware wallets is no longer fully trustworthy!
The problem with xpubs
With an "xpub", an extended public key, all addresses of an account in a Bitcoin wallet can be derived. In a multisig setup, the cosigners must therefore exchange these keys with each other in order to be able to generate addresses at all. This exchange is forced to take place via a software wallet on a smartphone or computer, as the hardware wallets cannot talk to each other directly.
An individual cosigner therefore receives information about the other cosigners indirectly via the software wallet, which simply has to be accepted. It is solely up to the user to ensure that the information from the other cosigners has been passed on correctly by the software wallet. If this is not done, the software wallet can, similar to the first pitfall, foist fake public keys on you.
This either enables an attack by blackmail, as described above, or even worse: in this scenario, the software wallet can forge two of the three public keys and thus gain full control over the addresses generated by the hardware wallet.
The supposedly secure multisig wallet would therefore be no better than an ordinary hot wallet.
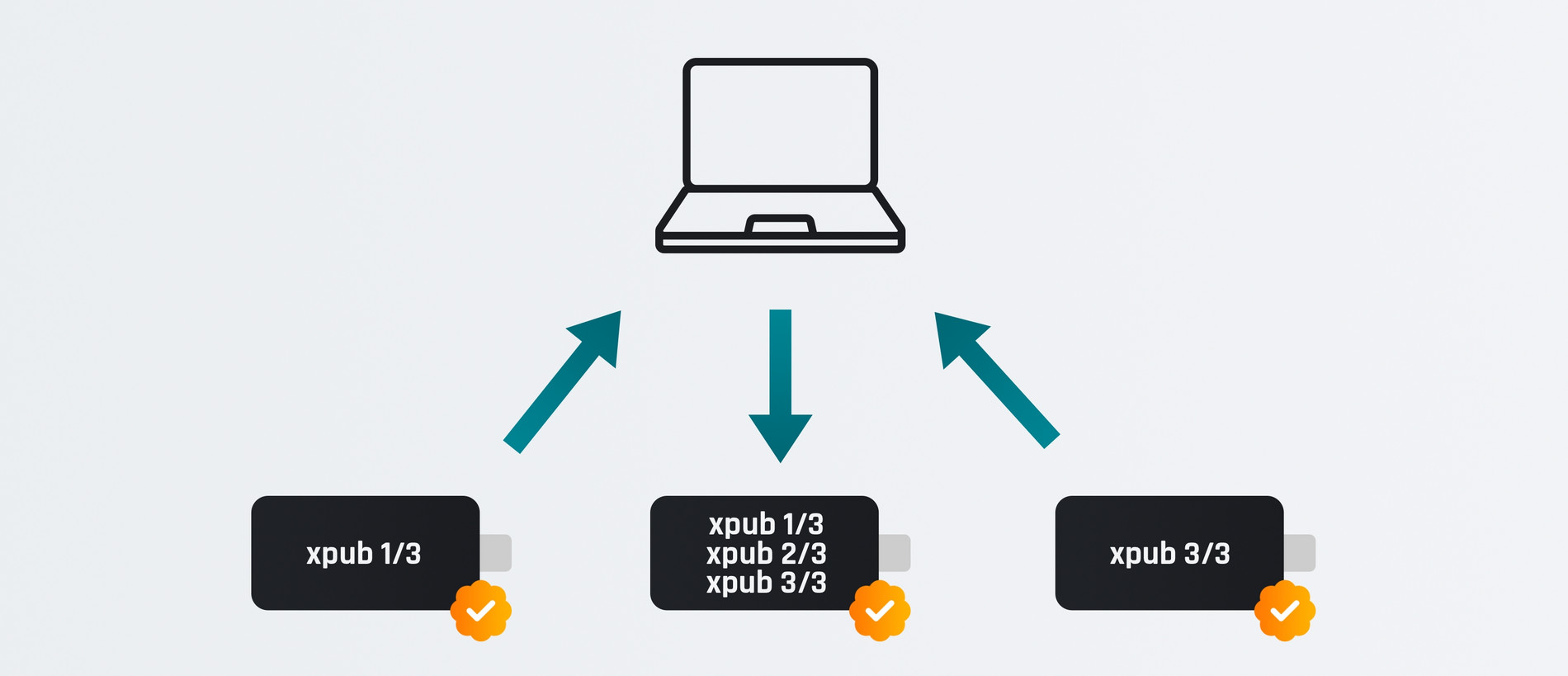
To rule out this vulnerability, the user must first verify each extended public key individually on the hardware wallet displays. This allows each cosigner to be correctly assigned to an xpub.
In the next step, the user must verify the public keys of the other cosigners on the hardware wallet, which will later also generate addresses, by comparing them with each other. After all, the software wallet theoretically has the option of passing on incorrect keys, which would be noticed immediately at this point.
Only after this successful verification can the address displayed on the hardware wallet, here in the middle, be trusted:
Note: With multisig wallets, it is not so easy to establish trust in receiving addresses, as this always depends on all cosigners and their secure communication with each other. Careful verification of the individual public keys and mutual checks to ensure that they have been passed on correctly are crucial in order not to jeopardize the security of the setup.
The choice of hardware wallets
The steps just described for checking receiving addresses are easier said than done. This is because some hardware wallets do not offer the necessary functions, such as displaying the cosigner xpubs, and should therefore not be used in a multisig setup in the first place.
Furthermore, a completely manual check is anything but practical in the long term. Users are unlikely to go through the procedure described above again and again for every address they want to use. Sooner or later, users are likely to become careless.
Hardware wallets that are used for a multisig setup should therefore memorize all cosigners after setup in order to remain trustworthy in the future without additional manual verification. This is also referred to as the "registration" of a multisig setup. This function is offered by BitBox02 or Blockstream Jade, among others. At the same time, this also eliminates another stumbling block, namely the automatic verification of exchange addresses, which are often required for transactions due to Bitcoin's UTXO model and would otherwise also have to be checked manually by the user.
Conclusion
Anyone looking for a beginner-friendly option for greater safety should think twice about whether Multisig is really the first choice. Many pitfalls are not obvious at first glance and it is easy to be lulled into a false sense of security, which is dangerous.
After this article, however, your senses should be a lot sharper and nothing should stand in the way of using a multisig wallet responsibly. The only important thing is not to become careless and to question your own setup from time to time.
Less complex and error-prone solutions for more security are possible with a relatively simple splitting of the mnemonic or the use of an optional passphrase. But the same applies here: always inform yourself thoroughly so that you don't inadvertently put your own Bitcoin at risk!

BitBox02
- Fully open source
- Secure chip
- USB-C support
- Bitcoin-only edition
- Anti-Klepto protection
- Secure multisig
- Not compatible with iOS/iPhone
- Backups can be saved on microSD card
- Get 5% discount with code BLOCKTRAINER

Blockstream Jade
- Attractive pricing
- Fully open source
- QR code scanner
- Compatible with iOS/iPhone (Bluetooth LE)
- Anti-Klepto (in USB/Bluetooth mode)
- Secure multisig
- No on-board secure chip
- Usable in two modes (QR or USB/BLE)
- Supports the Liquid sidechain